It depends on the mode of use of the service. Our security consultants will guide you through the entire Blindspot deployment process. They will test the deployment and confirm the operational readiness of the service.


DDoS protection as a 24/7 service
Blindspot provides complete DDoS protection.It includes state-of-the-art components for attack detection and mitigation. All backed by our global network and data centers.
How Blindspot works
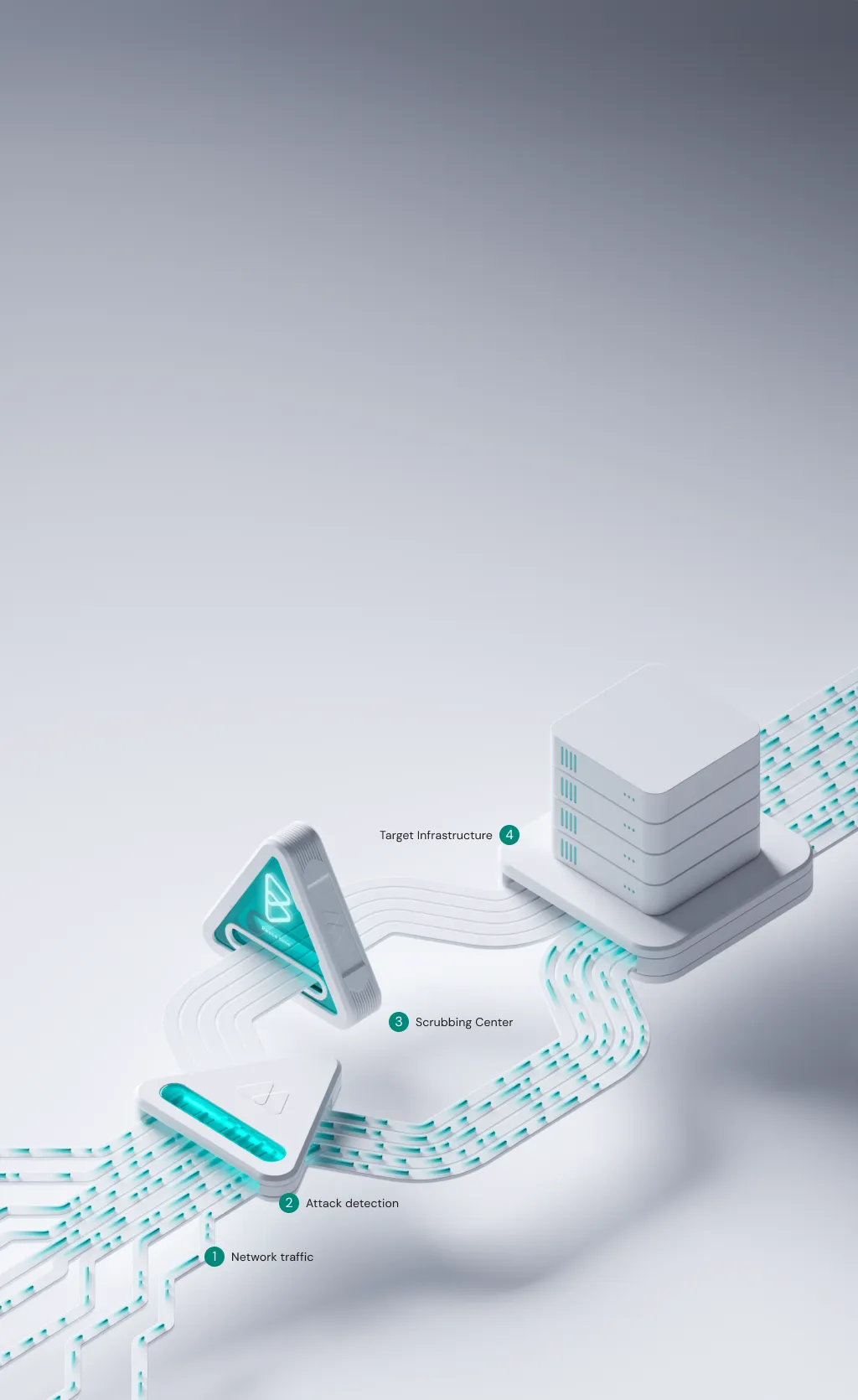
The key to an effective defense against DDoS attacks is correctly detecting the attack. Blindspot evaluates network traffic 1 in real-time and uses unique behavioral analysis and machine learning technology to find anomalies. Once it automatically detects an attack 2 it redirects the traffic to a scrubbing center 3 and begins iteratively generating dynamic signatures until all attack vectors are fully repelled and sent to target infrastructure 4
Automatic adaptive detection is a key element in the overall system, followed by other Blindspot components.